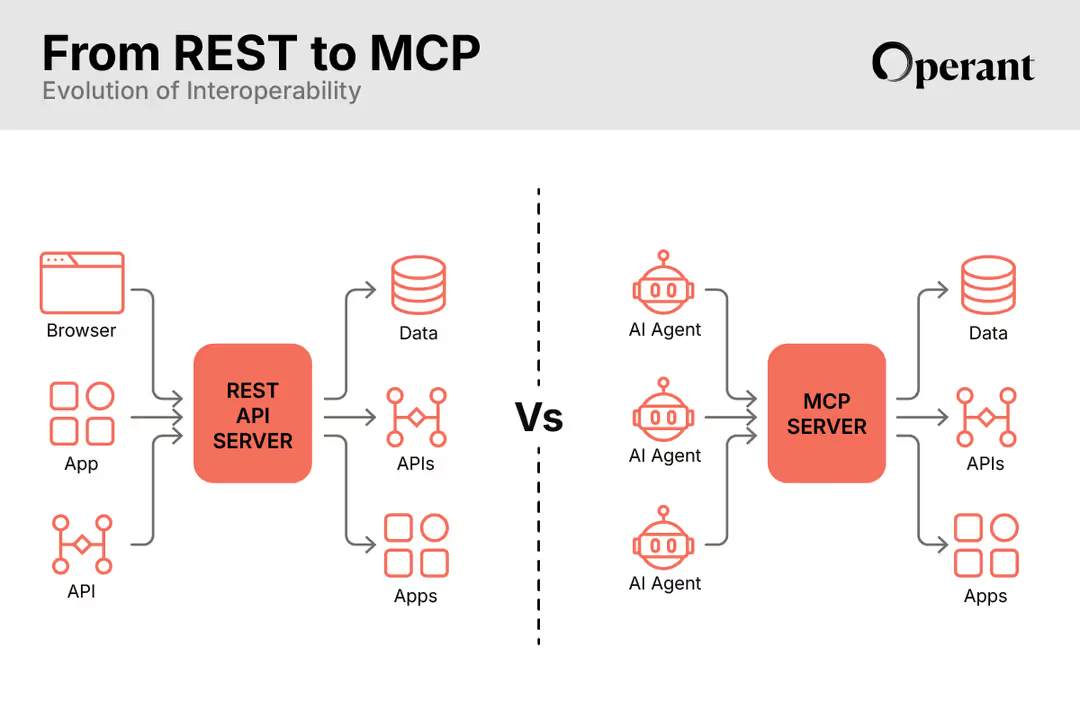
Active API Threat Protection
Bring API Security beyond the WAF with runtime protection for every API, Internal to External and Ingress to Egress
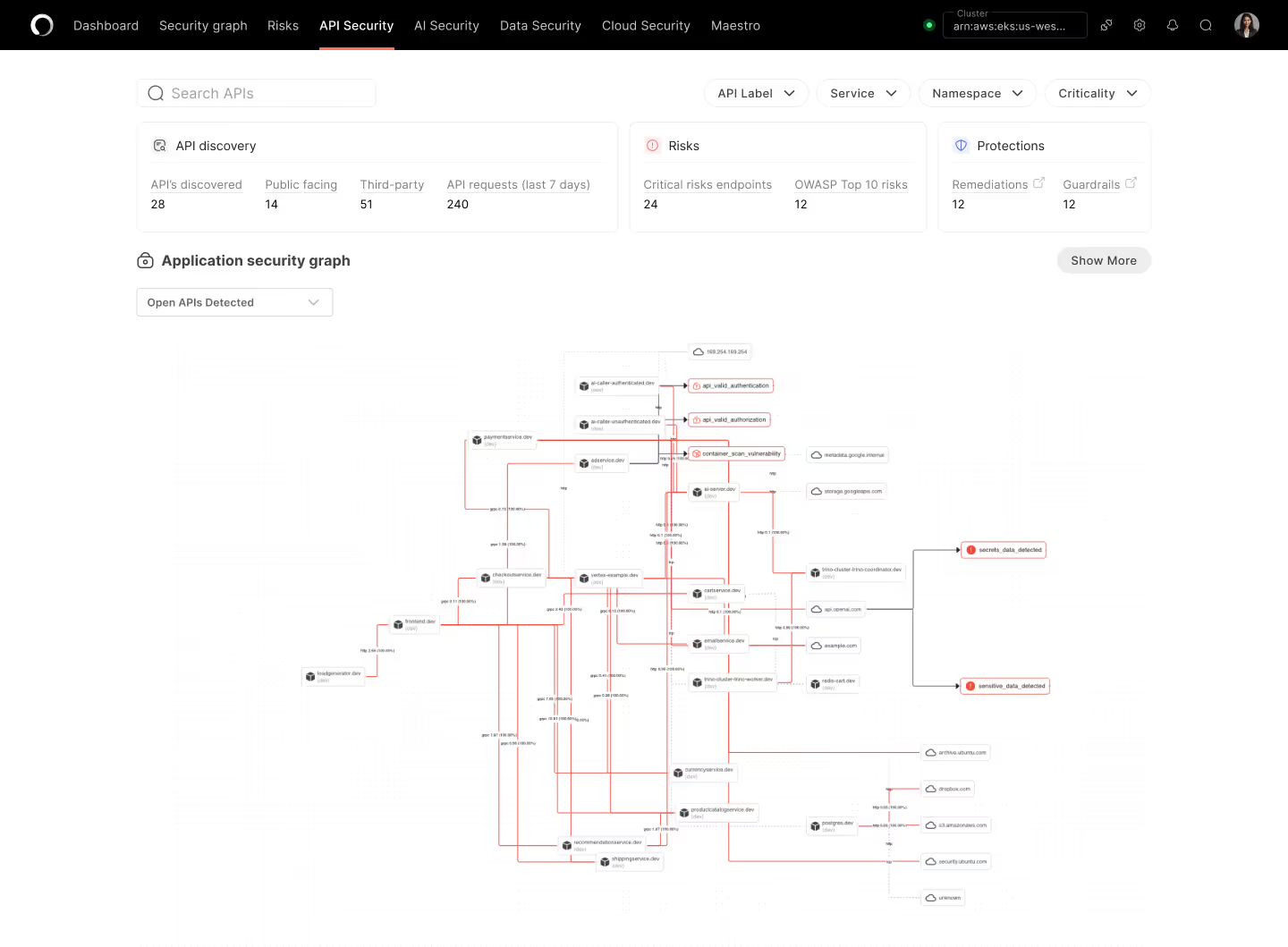
Discover and protect every API in your application environment

Vulnerability Scanning for APIs
Open API Graphs & Attack Paths
Inline API Threat Protection
Stop wasting time on static scanners and manual API testing, get automatic API catalogs, real-time insights on vulnerabilities, and prioritized runtime risks from internal, legacy and third party APIs.
Get an instant view of your entire live API blueprint, across dev, staging and prod. With an intuitive graph interface, fly through risk, context, and threat models for public and internal API endpoints.
API protection doesn't have to stop at a WAF. Protect your internal and 3rd party API interactions with K8s-native controls for protocol specific authentication, authorization, traffic rate limiting, API to API microsegmentation, and more.
Skip the POC.
Deploy Operant Today.
Single step helm install.
Zero instrumentation. Zero Integrations.
Works in <5 minutes.
Save time and money while securing your entire API nervous system
Make Every API More Secure
Do More With Less
Reduce Costs & Tooling Overload
Scale Applications Faster
Operant discovers and blocks the Top OWASP API Risks
OWASP API Top 10 Risks
Operant Coverage:
Broken Object Level Authorization
Unauthorized access to other users’ objects can result in data disclosure to unauthorized parties, data loss, or data manipulation. Under certain circumstances, unauthorized access to objects can also lead to full account takeover.
Broken Authentication
Attackers can gain complete control of other users’ accounts in the system, read their personal data, and perform sensitive actions on their behalf. Systems are unlikely to be able to distinguish attackers’ actions from legitimate user ones.
Unrestricted Resource Consumption
Exploitation can lead to DoS due to resource starvation, but it can also lead to operational costs increase such as those related to the infrastructure due to higher CPU demand, increasing cloud storage needs, etc.
Broken Function Level Authorization
Exploitation requires the attacker to send legitimate API calls to an API endpoint that they should not have access to as anonymous users or regular, non-privileged users. Exposed endpoints will be easily exploited. Such flaws allow attackers to access unauthorized functionality. Administrative functions are key targets for this type of attack and may lead to data disclosure, data loss, or data corruption. Ultimately, it may lead to service disruption.
Unrestricted Access to Sensitive Business Flows
Exploitation usually involves understanding the business model backed by the API, finding sensitive business flows, and automating access to these flows, causing harm to the business. In general technical impact is not expected. Exploitation might hurt the business in different ways, for example: prevent legitimate users from purchasing a product, or lead to inflation in the internal economy of a game.
Server Side Request Forgery
Exploitation requires the attacker to find an API endpoint that accesses a URI that’s provided by the client. In general, basic SSRF (when the response is returned to the attacker), is easier to exploit than Blind SSRF in which the attacker has no feedback on whether or not the attack was successful. Successful exploitation might lead to internal services enumeration (e.g. port scanning), information disclosure, bypassing firewalls, or other security mechanisms. In some cases, it can lead to DoS or the server being used as a proxy to hide malicious activities.
Security Misconfiguration
Attackers will often attempt to find unpatched flaws, common endpoints, services running with insecure default configurations, or unprotected files and directories to gain unauthorized access or knowledge of the system. Most of this is public knowledge and exploits may be available. Security misconfigurations not only expose sensitive user data, but also system details that can lead to full server compromise.
Improper Inventory Management
Attackers can gain access to sensitive data, or even take over the server. Sometimes different API versions/deployments are connected to the same database with real data. Threat agents may exploit deprecated endpoints available in old API versions to get access to administrative functions or exploit known vulnerabilities.
Unsafe Consumption of APIs
The impact varies according to what the target API does with pulled data. Successful exploitation may lead to sensitive information exposure to unauthorized actors, many kinds of injections, or denial of service.



3%20%3D(Art)Kubed%20(16%20x%209%20in)%20(7)-p-1080.avif)