Cloud-Native Application Protection at Runtime
Operant goes beyond cloud infra security to actively shield every layer of your applications at runtime
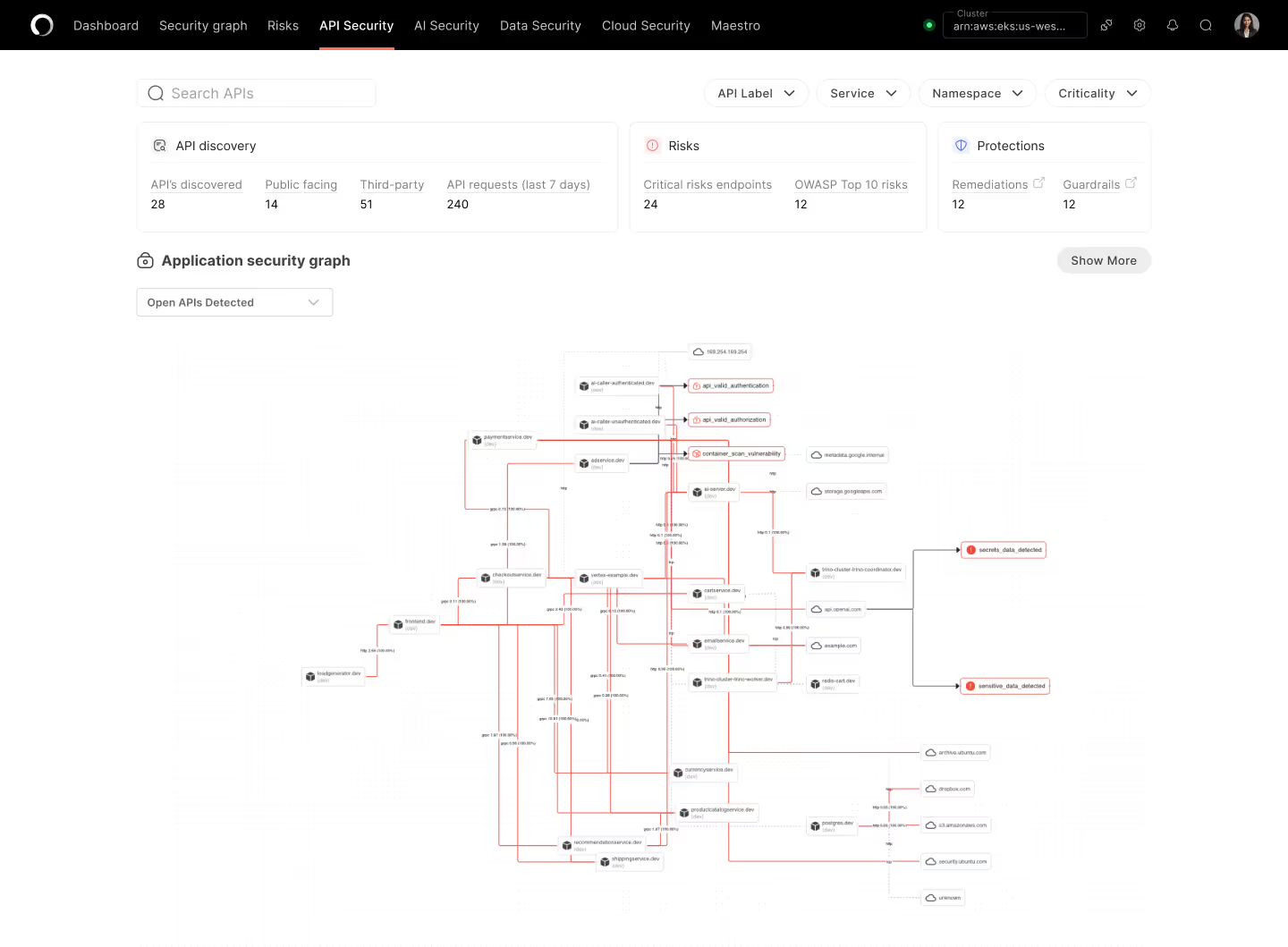
Defend your "cloud within the cloud" in real-time
Attack paths are not limited to the cloud layer, but most CNAPPs are
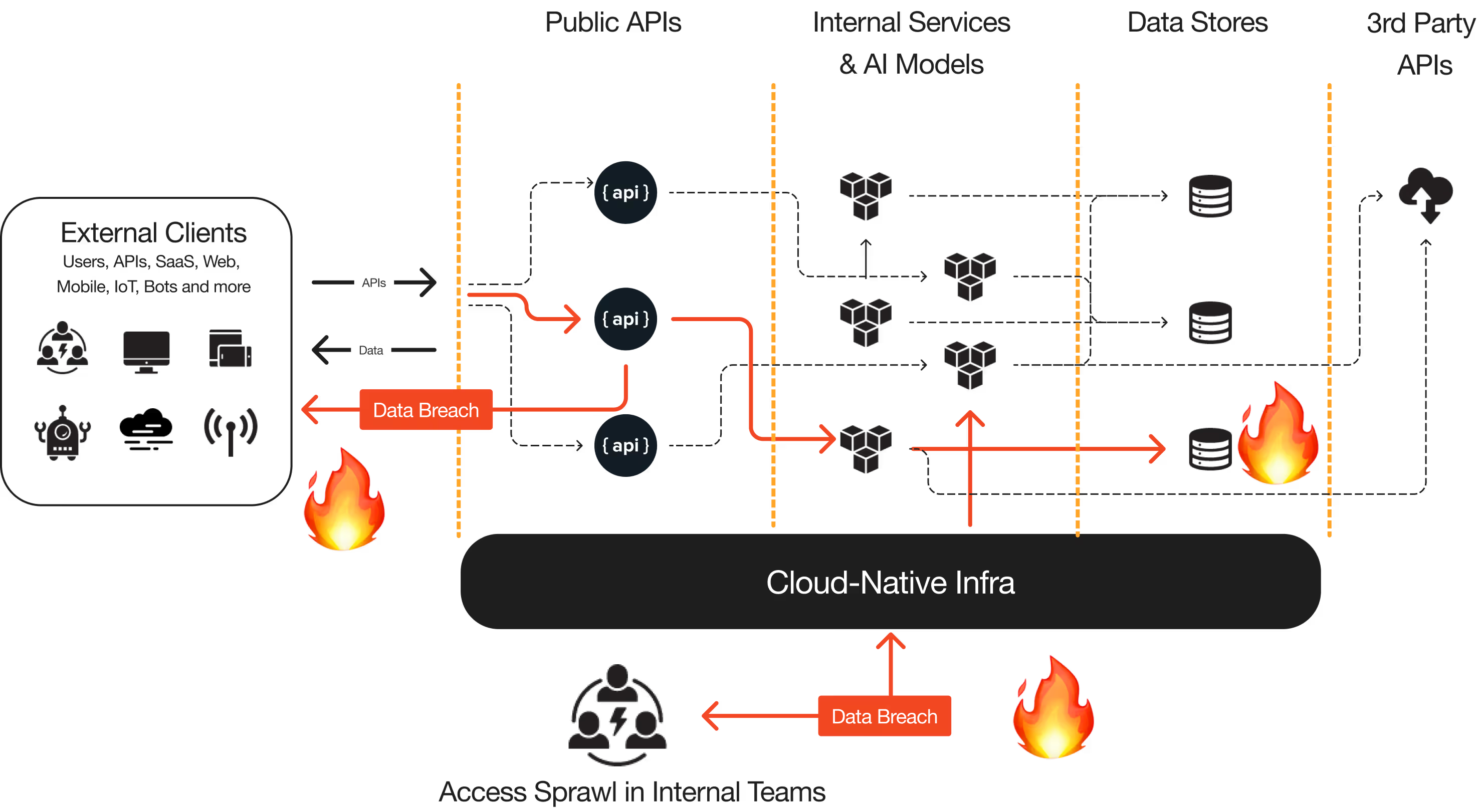

Live telemetry across *all* layers
Detections with Runtime Context
Runtime Threat Deterrence
With automatic telemetry that does not depend on manual instrumentation and costly integrations, Operant instantly builds the runtime blueprints of what's happening across ALL layers.
Instead of shipping the burden of logs and alerts to your team, SOC or SIEM, Operant intelligently builds the Runtime Context necessary for mitigating the most critical threats.
Moving beyond static infra layer dashboards or noisy eBPF sensors, Operant's runtime threat deterrence actively protects your live applications against a wide range of modern attacks.
Skip the POC.
Deploy Operant Today.
Single step helm install.
Zero instrumentation. Zero Integrations.
Works in <5 minutes.
Save time and money while protecting your entire cloud application stack
Active Protection for the Entire Product
Amplify Security Without More Work
Reduce Costs & Complexity
Accelerate Business Growth
Operant puts the Protection in CNAPP
The lines between cloud infra and applications are illusions
Operant crosses the invisible barrier to protect cloud applications in their native environments across every layer from infra to L7+, from prompts to processes.
Single-Step, Zero-Instrumentation Deployment
Deploy in minutes without the need for complex integrations or instrumentation, so you can see value immediately without impacting workflows.
Purpose-Built for Cloud-Native Environments
Operant integrates seamlessly into Kubernetes and other cloud-native infrastructure, enabling proactive, frictionless defense where data breaches actually happen.




3%20%3D(Art)Kubed%20(16%20x%209%20in)%20(7)-p-1080.avif)







